In today’s digital landscape, cybersecurity threats are becoming increasingly more sophisticated and pervasive. According to Mandiant’s M-Trends 2024 Report more than half of all detection sources came from an external detection and according to IBMs Cost of Data Breach Report 2024, the average time it took for companies to identify and detect a breach averaged at 258 days. For security professionals, the ability to effectively investigate potential threats is crucial in determining attack techniques, vectors, and motives. Enter Cyberscape, a cutting-edge threat modeling and graph-based investigation tool that is designed to streamline the investigate process for security professionals. Cyberscape allows for analyst to rapidly and comprehensively review Indicators of Compromise (IOCs) in order to draw meaningful insights into potential threats. Cyberscape helps companies decrease the effort needed to confirm a possible attack and subsequently allows them more resources to thwart the attack.
Understanding the Role of IOCs in Cybersecurity Investigations
Why IOCs Matter
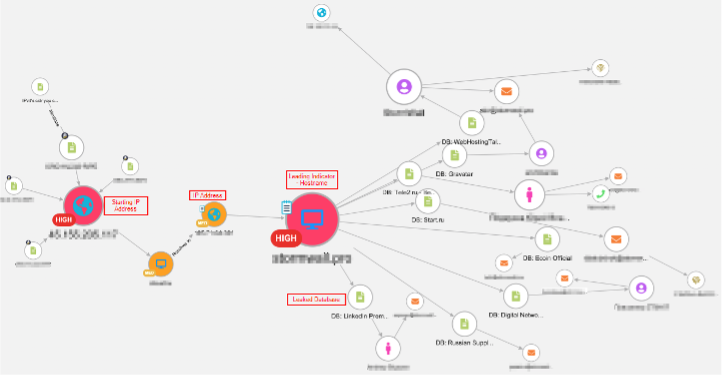
IOCs can be thought of as breadcrumbs that are left behind by any suspicious or malicious activities. Analyst can use these IOCs to help consider the scope of attacks, reconstruct attack vectors, and use them to prevent future attacks. Cyberscape leverages IOCs, referred to as “nodes,” to help analysts visually map out an attack.
Analysts can customize these nodes based on indicator values identified within their own environments. Subsequently, they can run “enrichments” on the IOCs, which reveal quick and actionable reputation data. This enriched data is invaluable for constructing a comprehensive and insightful investigation graph, enabling analysts to effectively understand and mitigate threats. By integrating these capabilities, Cyberscape empowers analysts to not only visualize and assess current threats but also to fortify their defenses against future attacks.
The Integration Process
However, IOCs are not the end all be all during the investigative process. For an analyst to accurately conclude an attack, they must combine IOCs with comprehensive OSINT Data and Tactics, Techniques, and Procedures (TTPs). This integration process is often time consuming and done manually. However, Cyberscape rapidly draws connections between these three necessary data sets, driving automation during an investigation workflow.
Cyberscape integrates an array of leading threat intelligence platforms and cybersecurity vendors into a cohesive, actionable, and insightful graphical interface. By consolidating disparate threat feeds into a single, coherent graph, Cyberscape empowers analysts to discern patterns, identify correlations, and derive strategic insights, ultimately enhancing their capability to preemptively address and mitigate emerging cybersecurity threats.

Example: A cybersecurity analyst detects a suspicious IP address within network traffic that is engaging in external communication. The analyst imports this IP into Cyberscape and leverages various enrichment sources to enhance the data. These sources promptly reveal that the IP address has a malign reputation. Further enrichment utilizing a dark web monitoring source uncovers that the IP is part of a larger botnet, establishing connections with previously reported Indicators of Compromise (IOCs) from diverse sources. Ultimately, the analyst consolidates this enriched information to uncover the potential techniques employed in the attack, thereby gaining deeper insights into the threat landscape.
How Cyberscape Simplifies Threat Analysis
Cyberscape’s automated IOC correlation feature is a game-changer for analysts, enabling them to quickly identify relationships between diverse data points. This capability provides a clearer and more comprehensive picture of the threat landscape, saving significant time and effort. Analysts no longer need to switch between multiple tools to connect the dots, as Cyberscape seamlessly integrates this functionality, making threat detection more efficient and accurate.
Progressive Construction with Attribute Mapping
Tagging techniques and progressive construction capabilities allow analysts to visualize large-scale attacks on their organization. Analysts can intuitively and creatively tag nodes within the graph to establish essential connections and references, enhancing the investigative process. Additionally, Cyberscape progressively maps nodes and allows investigators to comprehensively view the threat landscape. Visualization helps in understanding the full scope of an attack, enabling proactive defense strategies and more informed decision-making.
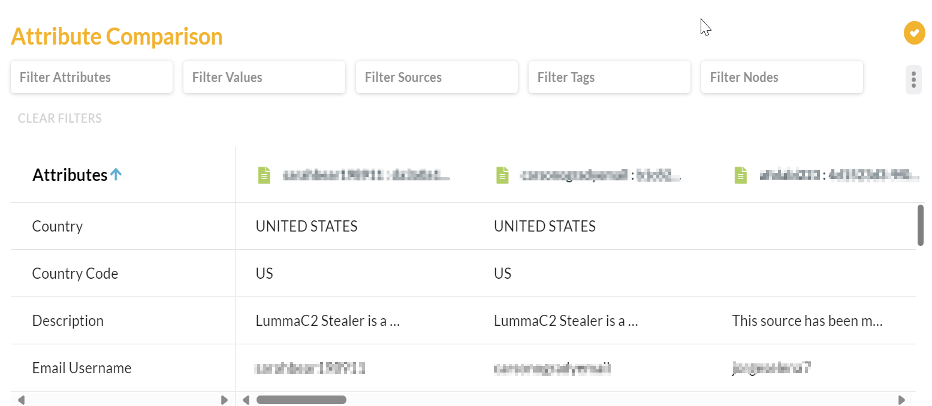
Attribute Clustering
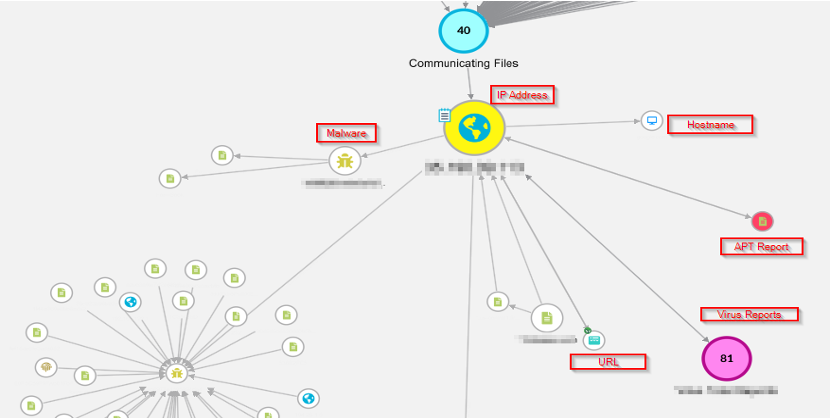
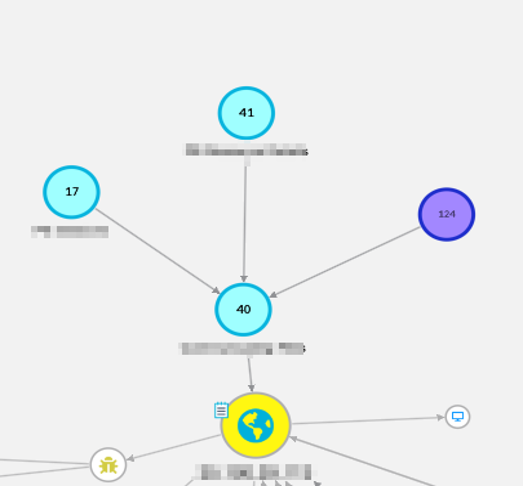 The capability to cluster scenarios equips analysts with a robust method for identifying potential multi-staged attacks. Cyberscape autonomously generates clusters according to the enrichment parameters specified by the analyst. This feature categorizes each node based on its attributes, enabling analysts to efficiently review and evaluate these attributes for any indications of malicious activity. Additionally, analysts are able to manually cluster results of enrichments to better visualize an active investigation.
The capability to cluster scenarios equips analysts with a robust method for identifying potential multi-staged attacks. Cyberscape autonomously generates clusters according to the enrichment parameters specified by the analyst. This feature categorizes each node based on its attributes, enabling analysts to efficiently review and evaluate these attributes for any indications of malicious activity. Additionally, analysts are able to manually cluster results of enrichments to better visualize an active investigation.
Anomaly-Based Detection
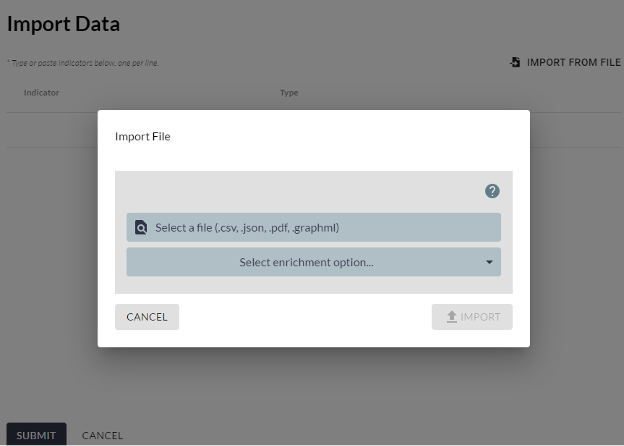
Threat actors are continuously evolving their tactics to conceal their attack techniques and vectors amidst extensive volumes of log data. In this context, anomaly-based detection emerges as a potent strategy to mitigate such challenges. Cyberscape’s log import feature empowers analysts to visualize event-based anomalies effectively. By enabling the rapid ingestion of logs, this feature facilitates the assessment of Indicators of Compromise (IOCs) within both internal and external environments, thereby enhancing the capacity to identify sophisticated threats that might otherwise remain undetected. Analysts can review their event logs from both a larger and graphical perspective or a more granular and itemized perspective.
Drawing Insights and Making Connections
The foremost objective of any cybersecurity investigation is to derive actionable insights that inform strategic responses and to comprehend the broader implications of identified threats. This involves not only detecting and mitigating immediate risks but also understanding the underlying patterns, motivations, and potential future impacts of these threats. By achieving a nuanced understanding of the broader threat landscape, cybersecurity professionals can enhance their defensive measures, anticipate potential attack vectors, and contribute to the overall resilience of the organization’s security posture.
Visualization Tools
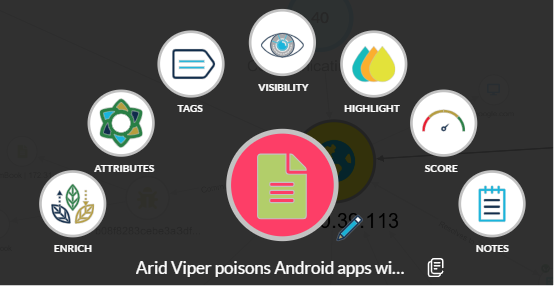
Maintaining organization throughout an investigation is crucial for analysts to reach the most accurate and timely conclusions. To support this endeavor, Cyberscape incorporates a suite of built-in visualization tools. Cyberscape offers tools, such as graph-based mapping, to help investigators see connections between IOCs and potential threat actors. Analysts can also swiftly modify the visual attributes of a node, adjusting its visibility, highlighting it, assigning a low, medium, or high score, and appending personal annotations.
Real-Time Team Collaboration
Cybersecurity is a team sport. Cyberscape realizes this, and in an effort to foster active teamwork and coordination, allows analysts to actively make changes, comments, and share workspaces in real time. Investigations are frequently high-pressure and time-sensitive endeavors. The ability to collaborate with others in real time alleviates these challenges and facilitates the identification of potential missing links. Furthermore, all modifications to a workspace are recorded in an activity log, ensuring robust governance and providing other analysts with the opportunity to review any alterations made.
Proactive Defense
Cybersecurity investigations should cultivate a proactively defensive security posture. To derive real value from an investigation, analysts must be able to prioritize Indicators of Compromise (IOCs) that demand the most attention or immediate remediation efforts. Cyberscape significantly contributes to this practice by facilitating the seamless transition of IOCs to remediation efforts within an organization’s internal environment through the exporting of attribute lists.
Moreover, Cyberscape enhances the prioritization of remediation efforts by combining team collaboration with advanced visual customization. This synergy enables analysts to highlight critical nodes, adjust visibility, and annotate with personal notes, thereby ensuring that remediation actions are both informed and prioritized effectively. Additionally, Cyberscape empowers analysts to gather a comprehensive understanding of an attack on their organization by building a detailed data trail using layering techniques. This holistic approach allows for the visualization of interconnected IOCs and potential threat actors, offering a full picture of the attack and supporting a well-informed, strategic response.
In essence, Cyberscape not only aids in identifying and prioritizing IOCs but also fosters a collaborative and visually intuitive environment that enhances the overall efficacy of cybersecurity investigations and remediation efforts.
Conclusion
As cyber threats continue to evolve, the ability to conduct thorough and efficient investigations remains a cornerstone of effective cybersecurity strategy. In summary, the art of investigating cybersecurity threats hinges on the effective analysis of IOCs, matching their reputation through OSINT, and studying TTPs related to IOCs as a larger part of a working threat landscape. Cyberscape’s robust features and intuitive interface make it an invaluable tool for cybersecurity professionals seeking to draw meaningful connections and insights into potential threats. By leveraging Cyberscape, organizations can enhance their threat detection and response capabilities, ultimately safeguarding their digital assets.
Ready to elevate your cybersecurity investigations?
Explore Cyberscape today and see how it can transform your approach to threat analysis.